Cicada 3301 2014 Main articles and Subpages
Main articles:
- 2016 PUZZLE; POSSIBLE BACKREFERENCE TO 2014 PUZZLE >NEWEST CLUES<
- MAIN CICADA 3301 2014 PAGE PART 9 >NEW DISCOVERIES<
- MAIN CICADA 3301 2014 PAGE PART 8 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 7 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 6 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 5 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 4 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 3 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 2 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 1 ACTIVE
Subpages: Hot Links:
- Recent Wikia Changes
- Useful online tools, Runes decoder added
- We found traces of some Cicada Crypto group from 90s
- Outguess visual analysis, or do we have outguess on page 4 and 6? <<< table and RAR of all images files from Cicada 3301 2012-2014.
Warm Links:
- Loose ends (all things we never used)
- List of all Words, phrases and Primes mentioned in 2014 puzzle <<< all dictionaries
- Runes Transcription
- 2014 THINGS THAT HAD BEEN XORED (please put in things you tried)
- XOR 2014 tips
- Outguess tutorial
- suomynona's Fibbonachi and Runic information
- D_Synapse's Golden Cicada&Journey to the West
- Wikia community discusion
- Who is Wind, wind, or wind_ and why so many people are talking about her?
- Few logs and details about factorizing operation
- GPG Gnu Privacy Guard
/dev/random
- Post of the day
- CICADA 3301 2014 PUZZLE FACTS THE END JOKES
- Good luck 3301 background and custom CSS
- www.3301.eu is fake
- Wikipedia Cicada 3301 article
'Some other groups and pages
- Team Cicada Google+
- Team PiratePad
- Numinit gist page
- Henrik Falk blog with quick no junk explanation
- Facebook group
- Hack Forums
If you want to add your link on this menu PM Lurker69
START: cca 07:30 GMT 6th JAN 2014
The following link is the Twitter account from which the automated tweets were sent last year (2013).
https://twitter.com/1231507051321
From that Twitter account came the first image of Cicada 2014 which is as follows:
ADDITIONAL INFORMATION
Resolution: 547*577
http://i.imgur.com/zN4h51m.jpg
Uploaded to: http://prntscr.com/2gy9v1
OutGuess steganography software output: http://pastebin.com/raw.php?i=7ruHyAdB
Quick edits for now, will update with full write up later.
UPLOADED ON:
- http://prntscr.com/2gy9v1 imgur
- http://prntscr.com/2gy9y5 twitter
- (printscreen made at 7:39 GMT jan 6th
- in time zone: Central European Time Zone (UTC+01:00)
- local time: 08:40 AM
SIDE NOTE

After running the original image through Paint.net 3bit steganography plugin a cicada was revealed. (It can also be seen by simply adjusting the brightness and contrast.)
- it is just dark gray cicada on black background, if you set your monitor colors correctly it should be visible on i.imgur.com/zN4h51m.jpg
This is most likely nothing, as cicadas are a common motif.
FILE NAME
The original image was named as follows:
zN4h51m.jpg
Although there is no solid foundation as yet to suggest the filename is anything other than a re-upload, it may be worth while putting the name of the file to one side.
zN4h51m
FILENAMES ON IMGUR ARE RANDOM
- Cicada had no infuence on filename while uploading file.
JPEGsnoop
zN4h51m.jpg - http://pastebin.com/16Cn3jw2
Image Forensics
http://www.map-base.info/forensics/report_1/index_uk.sht 8:3:8:6 48:5:14:2 21:13:4:1 25:1:7:4 15:9:3:4 1:1:16:3 4:3:3:1 8:3:26:4 47:3:3:5 3 13:2:5:4 1:4:16:4 . o n i o n Good luck. 3301
-----BEGIN PGP SIGNATURE----- Version: GnuPG v1.4.11 (GNU/Linux) iQIcBAEBAgAGBQJSyjguAAoJEBgfAeV6NQkPsgAP/A3tMC3lpyFNAc/sj+Izu15S CzUjZJMe20Gu9UMNokQ2UJabktv9w0GMyK17TrMkUcU+ZpjdzGNqKoE2ETVxLmD/ uBZtR5PnF9EE3D08tJUPN1vSrYNkYk+9zcaUJZMPNgYNCt/CACutPwrOci9i9FDO 7BIpnhGqT3ZruqrSwO2Y73LJI1xxUt1XUqh1NQ+fJeAFMRkJBZZazkxRlgk3GGsF fLrcEKrS+KBipV1EQaaKxjISc9hc2c1TfxE66evlkN+zLcoyDcYuyruNM5wiZzgM 2uR58c+xgWQgG5UuLFClfvjDxUvDkrKt4mzEeaYSUm1MsYueuYklz4ydlg5Mf6l2 p1WyAxO52XfXVUZASk6VmaEQ0WjODTXvLeFTxUSDoKDMkvxDVxX6wGkufS9JwakB nTZizZ8Ypv8GcNCuNNGd6gZ1Vk2MYntggXdX8INd0Itcd3QnLqbBnATDOinDxlOs 5zTrtyTHNaxxDagPfAbU1jMXM0aHd7PFAzjjp7kgCTWqMyBch+8Vt80bjkdL9iw8 Q3hxuanq8mh6nUGc+tNe0UfqKHEbE+jWIezYqgawJB0M9R5OhxWE+E+jPXtZKkXQ JHYndPDrrsV8q27b7p0KN0+oblTkjqsItIAuLu7FNd0B4xb1jjp1Sbh7WJdZ/rbi mCO0vN/obU9qK1Vfapy0 =6Gxk -----END PGP SIGNATURE-----
OUTGUESS DECYPHER WALKTHROUGH
- Using Outguess run the following command:
outguess -r /path/zN4h51m.jpg /path/zN4h51m.txt
- Replace '/path/' with the directory structure location of where you want your file to output to. After the output location, name your file whatever you want with a .txt file extension.
- WInfags use win binnaried in wikia or CYGWIN
Cypher = x:x:x:x (paragraph:sentence:word:letter) PART 1 The work of a private man who wished to transcend, He trusted himself, to produce from within.
Which leads to - http://www.math.dartmouth.edu/~doyle/docs/self/self.pdf
Cypher = x:x:x:x (paragraph:sentence:word:letter)

PART n i o n
Which is equal to - auqgnxjtvdbll3pv.onion or http://auqgnxjtvdbll3pv.onion/
- or clernet adress
Good luck. 3301 -----BEGIN PGP SIGNATURE----- Version: GnuPG v1.4.11 (GNU/Linux) iQIcBAEBAgAGB...
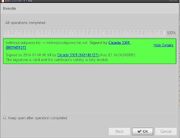
PGP
Signature of image is valid:
thumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdfthumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdftoem references transcendentalism
Emerson is a noted transcendentalist author "he trusted himsef" refers to "trust thineself", which is a theme throughout Self-Reliance, as is producing from within Italic text==ONION NO1 - For Every Thing That Lives Is Holy==thumb|link=https://www.blackhat.com/presentations/bh-europe-05/bh-eu-05-callas-up.pdf
http://auqgnxjtvdbll3pv.onion/

If you look closer to the image, there is the cicada symbol
[http://auqgnxjtvdbll3pv.onion/
]
- if you look closely at the image, there is a cicada symbol
- the center bottom (Ancient of Days) image is shifted two pixels to the right, and the right image is two pixels shorter than the canvas, leaving a 2 px wide vertical and horizontal strip of 415 and 293 pixels empty.
[http://auqgnxjtvdbll3pv.onion/
]

Error Level Analysis (ELA) Of Onion1 image
DEBATE ABOUT MEANING OF THE PICTURE ON ONION
FILE NAME
The original file name is:
On image center where (like in mirror ) dude places finger there are words vodo III(under line) and some code,photoshop boys where are u?... and on left image on second finger are some dot...?
1033.jpg
This may be notable (unconfirmed), as it is a mirror of 3301 i.e. Cicada 3301
1033 vs. 3301
JPEGsnoop
1033.jpg - http://pastebin.com/NNtsegga
HTML SOURCE CODE OF http://auqgnxjtvdbll3pv.onion/ (no linebreaks added)
(no linebreaks added)
<html><head><title>For Every Thing That Lives Is Holy</title><body><img src="1033.jpg" /></body></html>
HTML OF .onion RAW SOURCE CODE
<html> <head> <title>For Every Thing That Lives Is Holy</title>
<body> <img src="1033.jpg" />
</body> </html> *Note missing trailing </head> in source code
ALTERNATIVE IMAGE LOCATIONS
There's also this
HTTP BANNER ONION 1
HTTP/1.1 200 OK Date: Mon, 06 Jan 2014 14:24:13 GMT Server: Apache Last-Modified: Mon, 06 Jan 2014 07:43:43 GMT ETag: "9904-68-4ef486b41c9c0" Accept-Ranges: bytes Content-Length: 104 Vary: Accept-Encoding Content-Type: text/html
HTTP ETags ONION 1
auqgnxjtvdbll3pv.onion/1033.jpg: 98e5-53959-4ef4858107540
auqgnxjtvdbll3pv.onion: 9904-68-4ef486b41c9c0
OUTGUESS FROM 1033.jpg from ONION 1
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA1
Welcome.
Good luck.
3301
e = 65537
n = 75579125746085351644267182920580212556413102071876330957950694457000592\
10248050757270234679993673844203148013173091173786572116639
- -----BEGIN COMPRESSED RSA ENCRYPTED MESSAGE-----
Version: 1.99
Scheme: Crypt::RSA::ES::OAEP
eJwBswBM/zEwADE2MgBDeXBoZXJ0ZXh0LE2jxJS1EzMc80kOK+hra1GKnXgQKQgVitIy8NgA7kxn
2u8jNQDvlu0uymNNiu6XVCCn66axGH0IZ9w4Af3K/yRgjObsfA1Q7QqpXNALJ9FFPgYl5rh07cBP
M9kbSH6DynU/5cYgQod2KymjWcIvKx3FkjV4UOGakDnBf1eQp1uwvn3KxDVwTyzPqbMnZvOA06Ec
AfKtyz1hEK/UBXkeMeVrnV5SQQ==
=yTUshDMKN65aPaKAR0OU8g==
- -----END COMPRESSED RSA ENCRYPTED MESSAGE-----
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v1.4.11 (GNU/Linux)
iQIcBAEBAgAGBQJSyly/AAoJEBgfAeV6NQkPHhUP/R7nuYiTMw+3sbe0xV+4rmiN
liSDmW6ibOK4UTkZDTeAS5kAKIjxCC3DwWi0lXqBGZyabojWHM2wRwYLOhvfKvgg
DgPnW1BSZ/R67GaUy0CM/vtZOtktBeIdntlZamk9DpW5bQ311c7N9dy6uWc8+hOM
umkcnT7u799zESazFgCeDSOw0cFgHDiG9UTAQxbe+NsXY/NKm4N0WAtgWmdte5ym
dU8ImpmXWg8NChdn49UtuAACi8s8tcI/lHj1Yjh+AQRbO2+Ozn9eSxUAQ1TsXSgt
30jKmXI5ss4WHS16nYsS97BUbo4oX3NBXaCjSZb7fKO9CRJBo3gm2R8/NcIMIkEc
GlQ/7rCQWHXA0MC+415ut5dcJf2ihwid81c1xsDyqQdfhEsWE/wVnK7Ujje+BgcO
ybBHl8ejJzWhZkCvesHOmIo1RLEanxlGUC5jcRLqImrT7A9CrO+EVFW16EZpvzug
Tsopo56+JbIFiIzAq+CGujHgDZnoHJFtB574utjOnZz9xzsVZ3lirQyAFOGauH+g
K+XxjXjY8tT5lppAgmF3zWKqha7NoV+9FgFl2q2SS9ue+s4Joyn5PYKnICJeze3i
K9BZ7gIT694s4dLEzu6kGaRyuNmx8qaoDs0kjvEB5pI+1buGuNAysHQWIDyY3DWb
CjJ1AnBLY0ObxaMbWMR/
=d5E8
-----END PGP SIGNATURE-----
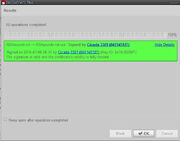
PGP VALIDATION
PGP Validates - http://prntscr.com/2h1cvj
thumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvjthumb|link=http://prntscr.com/2h1cvj
RSA THEORY
e = 65537
3.3.1. The rsa-sha1 Signing Algorithm
The rsa-sha1 Signing Algorithm computes a message hash as described
in Section 3.7 below using SHA-1 [FIPS.180-2.2002] as the hash-alg.
That hash is then signed by the signer using the RSA algorithm
(defined in PKCS#1 version 1.5 [RFC3447]) as the crypt-alg and the
signer's private key. The hash MUST NOT be truncated or converted
into any form other than the native binary form before being signed.
The signing algorithm SHOULD use a public exponent of 65537.
Source: http://www.ietf.org/rfc/rfc4871.txt
n = 75579125746085351644267182920580212556413102071876330957950694457000592\10248050757270234679993673844203148013173091173786572116639
Our n is 130 decimal digits long or 429 bit.
3.3.3. Key Sizes
Selecting appropriate key sizes is a trade-off between cost,
performance, and risk. Since short RSA keys more easily succumb to
off-line attacks, signers MUST use RSA keys of at least 1024 bits for
long-lived keys. Verifiers MUST be able to validate signatures with
keys ranging from 512 bits to 2048 bits, and they MAY be able to
validate signatures with larger keys. Verifier policies may use the
length of the signing key as one metric for determining whether a
signature is acceptable.
Factors that should influence the key size choice include the
following:
o The practical constraint that large (e.g., 4096 bit) keys may not
fit within a 512-byte DNS UDP response packet
o The security constraint that keys smaller than 1024 bits are
subject to off-line attacks
o Larger keys impose higher CPU costs to verify and sign email
o Keys can be replaced on a regular basis, thus their lifetime can
be relatively short
o The security goals of this specification are modest compared to
typical goals of other systems that employ digital signatures
See [RFC3766] for further discussion on selecting key sizes.
Source: http://www.ietf.org/rfc/rfc4871.txt
STEGDETECT
Stegdetect also detects jphide data inside this image
- Stegdetects commonly detects false positives
SIDE NOTE
For people who are not going to go the bruteforce way, they can check their p and q assumptions here: http://codeseekah.com/cicada/isp.php
It is important to note that p and q are not necessarily primes (i.e. nobody forced 3301 to use primes). (http://en.wikipedia.org/wiki/RSA_(cryptosystem)#Key_generation).
Also note that factoring will take a long time, so guessing might be a good approach as well - look at sets of emirps for example, there might be a 60-65 digit emirp/prime set out there that produces n.
WE ALMOST SAME PUZZLE IN 2012. But it was individualized, one before last one.
IF YOU RUN OUTGUESS ON THE IMAGE WITH KEY OF 3011 YOU GET THE FOLLOWING:
RSA
DAFUQ IS THIS RSA ? WHY DO WE HAVE TO FACTORIZE n ? HOW RSA KEY WORKS ?
- http://youtu.be/M7kEpw1tn50?t=54s
- https://www.cs.drexel.edu/%7Ejpopyack/IntroCS/HW/RSAWorksheet.html
- http://searchsecurity.techtarget.com/definition/RSA
- http://en.wikipedia.org/wiki/RSA_%28algorithm%29
- https://en.wikipedia.org/wiki/Primality_test
*p distinct prime number
*q distinct prime number
*n is used as the modulus for both the public and private keys. Its length, usually expressed in bits, is the key length.
(In cryptography, key size or key length is the size measured in bits of the key used in a cryptographic algorithm (such as a cipher).)
*e is released as the public key exponent.
RSA encryption and decryption
Assume that an RSA public key uses a modulus with j bits; its factors
are two numbers of about j/2 bits each. The expected computation
time for encryption and decryption are different. As before, we
denote the number of words in the machine representation of the
modulus by the symbol n.
Most implementations of RSA use a small exponent for encryption. An
encryption may involve as few as 16 squarings and one multiplication,
using n-by-n-word operations. Each operation must be followed by a
modular reduction, and therefore the time complexity is about 16*(.6
+ 1) + 1 + 1 ~= 28 n-by-n-word multiplies.
RSA decryption must use an exponent that has as many bits as the
modulus, j. However, the Chinese Remainder Theorem applies, and all
the computations can be done with a modulus of only n/2 words and an
exponent of only j/2 bits. The computation must be done twice, once
for each factor. The effort is equivalent to 2*(j/2) (n/2 by n/2)-
word multiplies. Because multiplying numbers with n/2 words is only
1/4 as difficult as multiplying numbers with n words, the equivalent
effort for RSA decryption is j/4 n-by-n-word multiplies.
If you double the size of the modulus for RSA, the n-by-n multiplies
will take four times as long. Further, the decryption time doubles
because the exponent is larger. The overall scaling cost is a factor
of 4 for encryption, a factor of 8 for decryption.
Source: http://tools.ietf.org/search/rfc3766#page-11
NFS FACTORIZATION
- http://gilchrist.ca/jeff/factoring/benchmark.html
- http://gilchrist.ca/jeff/factoring/nfs_beginners_guide.html
- http://gilchrist.ca/jeff/factoring/index.html
FACTORIZING CICADA 3301 PUZZLE n FOR REAL
TOGETHER AS ONE DIVIDED BY ZERO
Our best self-motivated coders distributed factorization among their boxes:
our heroes
- They used: http://cado-nfs.gforge.inria.fr/
- Number Field Sieve (NFS) algorithm.
- Currently on final step.
- Expect results "In Time."
- http://en.wikipedia.org/wiki/General_number_field_sieve
- I cant find any videos describing what NFS is
- http://www.youtube.com/watch?v=x_8YtOfKA0Q
- add if you find some
- http://primes.utm.edu/notes/rsa130.html
- Please read what GNFS is in respect to others doing hard work
13:36 <@mdzhb> PID28389 2014-01-07 05:27:44,557 Info:Lattice Sieving: Total CPU time: 878768.6999999997s 13:36 <@mdzhb> PID28389 2014-01-07 05:27:44,557 Info:Filtering - Singleton removal: Total cpu/real time for purge: 610.26/424.892 13:36 <@mdzhb> PID28389 2014-01-07 05:27:44,558 Info:Filtering - Merging: Total cpu/real time for replay: 43.01/37.4837 13:37 <@mdzhb> PID28389 2014-01-07 05:27:44,558 Info:Linear Algebra: Krylov: CPU time 34471.22, COMM time 954.22 13:37 <@mdzhb> PID28389 2014-01-07 05:27:44,559 Info:Linear Algebra: Mksol: CPU time 20060.39, COMM time 512.27 13:37 <@mdzhb> PID28389 2014-01-07 05:27:44,667 Info:Complete Factorization: Total cpu/real time for everything: 938758/18361
To all those who participated: YOU ROCK FOLKS! We did it!!!!!
SOLUTION GOES HERE SOLVED AT 07:39 GMT 7. 1. 2014
(23 hours after finding n, 8 hours of factorizing)
factors of n:
n= 7557912574608535164426718292058021255641310207187633095795069445700059210248050757270234679993673844203148013173091173786572116639
are:
sage: p = 97513779050322159297664671238670850085661086043266591739338007321 sage: q = 77506098606928780021829964781695212837195959082370473820509360759 sage: p.is_prime() True sage: q.is_prime() True sage: p*q confirmed!
NEXT STEP
Next step will be to use the two prime numbers, *p & *q, to recreate the private RSA KEY and decrypt the message:
-----BEGIN COMPRESSED RSA ENCRYPTED MESSAGE----- Version: 1.99 Scheme: Crypt::RSA::ES::OAEP eJwBswBM/zEwADE2MgBDeXBoZXJ0ZXh0LE2jxJS1EzMc80kOK+hra1GKnXgQKQgVitIy8NgA7kxn 2u8jNQDvlu0uymNNiu6XVCCn66axGH0IZ9w4Af3K/yRgjObsfA1Q7QqpXNALJ9FFPgYl5rh07cBP M9kbSH6DynU/5cYgQod2KymjWcIvKx3FkjV4UOGakDnBf1eQp1uwvn3KxDVwTyzPqbMnZvOA06Ec AfKtyz1hEK/UBXkeMeVrnV5SQQ== =yTUshDMKN65aPaKAR0OU8g== -----END COMPRESSED RSA ENCRYPTED MESSAGE-----
Script that does all this in one step:
- Script for decryption (insert correct p, q, e and encrypted message; this script plots "The Game" with the current p, q, e and encrypted message. Replace the values from the outguessed message)
- ! copy script from Raw Paste Data on bottom of pastebin page
- pastebin formatting from normal window causes:
- Uncaught exception from user code: Breached Armour.
- To fix it you have to move the my $plaintext and the message to the beginning of the line
- Winfags need: http://strawberryperl.com/ (dont forget to set paths: http://prntscr.com/2h0193)
HERE WE GO:
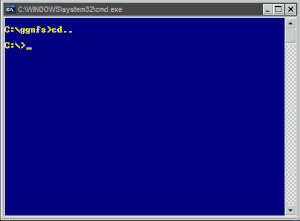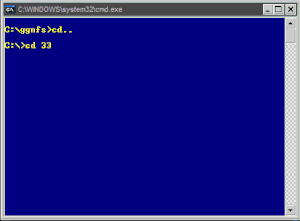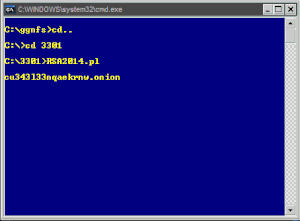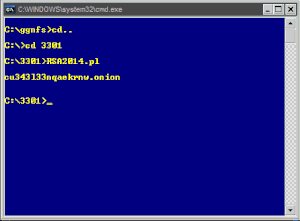
SCRIPT WITH p, q, and RSA ENCRYPTED MESSAGE inserted
DECRYPTED RSA MESSAGE:
939
THIS PAGE IS DISCONTINUED, READONLY NOW. PLEASE DONT EDIT IT ANYMORE.
TO CONTINUE GO TO ARTICLE PART 2
LINK TO CURRENT SITE WITH UPDATED PROGRESS
Cicada 3301 2014 Main articles and Subpages
Main articles:
- 2016 PUZZLE; POSSIBLE BACKREFERENCE TO 2014 PUZZLE >NEWEST CLUES<
- MAIN CICADA 3301 2014 PAGE PART 9 >NEW DISCOVERIES<
- MAIN CICADA 3301 2014 PAGE PART 8 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 7 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 6 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 5 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 4 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 3 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 2 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 1 ACTIVE
Subpages: Hot Links:
- Recent Wikia Changes
- Useful online tools, Runes decoder added
- We found traces of some Cicada Crypto group from 90s
- Outguess visual analysis, or do we have outguess on page 4 and 6? <<< table and RAR of all images files from Cicada 3301 2012-2014.
Warm Links:
- Loose ends (all things we never used)
- List of all Words, phrases and Primes mentioned in 2014 puzzle <<< all dictionaries
- Runes Transcription
- 2014 THINGS THAT HAD BEEN XORED (please put in things you tried)
- XOR 2014 tips
- Outguess tutorial
- suomynona's Fibbonachi and Runic information
- D_Synapse's Golden Cicada&Journey to the West
- Wikia community discusion
- Who is Wind, wind, or wind_ and why so many people are talking about her?
- Few logs and details about factorizing operation
- GPG Gnu Privacy Guard
/dev/random
- Post of the day
- CICADA 3301 2014 PUZZLE FACTS THE END JOKES
- Good luck 3301 background and custom CSS
- www.3301.eu is fake
- Wikipedia Cicada 3301 article
'Some other groups and pages
- Team Cicada Google+
- Team PiratePad
- Numinit gist page
- Henrik Falk blog with quick no junk explanation
- Facebook group
- Hack Forums
If you want to add your link on this menu PM Lurker69
