Cicada 3301 2014 Main articles and Subpages
Main articles:
- 2016 PUZZLE; POSSIBLE BACKREFERENCE TO 2014 PUZZLE >NEWEST CLUES<
- MAIN CICADA 3301 2014 PAGE PART 9 >NEW DISCOVERIES<
- MAIN CICADA 3301 2014 PAGE PART 8 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 7 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 6 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 5 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 4 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 3 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 2 DISCONTINUED
- MAIN CICADA 3301 2014 PAGE PART 1 ACTIVE
Subpages: Hot Links:
- Recent Wikia Changes
- Useful online tools, Runes decoder added
- We found traces of some Cicada Crypto group from 90s
- Outguess visual analysis, or do we have outguess on page 4 and 6? <<< table and RAR of all images files from Cicada 3301 2012-2014.
Warm Links:
- Loose ends (all things we never used)
- List of all Words, phrases and Primes mentioned in 2014 puzzle <<< all dictionaries
- Runes Transcription
- 2014 THINGS THAT HAD BEEN XORED (please put in things you tried)
- XOR 2014 tips
- Outguess tutorial
- suomynona's Fibbonachi and Runic information
- D_Synapse's Golden Cicada&Journey to the West
- Wikia community discusion
- Who is Wind, wind, or wind_ and why so many people are talking about her?
- Few logs and details about factorizing operation
- GPG Gnu Privacy Guard
/dev/random
- Post of the day
- CICADA 3301 2014 PUZZLE FACTS THE END JOKES
- Good luck 3301 background and custom CSS
- www.3301.eu is fake
- Wikipedia Cicada 3301 article
'Some other groups and pages
- Team Cicada Google+
- Team PiratePad
- Numinit gist page
- Henrik Falk blog with quick no junk explanation
- Facebook group
- Hack Forums
If you want to add your link on this menu PM Lurker69
A new message
After a long period of inactivity, at around 00:00 29/01/2014 UTC, Onion 4 came online again (after being offline for a period of time).
The content of the page was hex encoded output, similar to the rest of the data we've received from previous onions. A mirror of the content can be found here.
Things found on the onions: http://sigmaninestudios.com/3301
Another pastebin with links to onion 4 backups http://pastebin.com/uLT3drh2
HTML and string on onion 4 (jan 29th 2014)

nopd's printscreen of string on onion 4
onion 4 came online at 0:05gmt 29/01/2014
Hex posted on onion 4 was not plain hex string of 4 jpgs like we were used too. It was actually gzip file that needed to be decompressed to get string with jpgs.
Gzip files begin with 0x1F (ID1) 0x8B (ID2).
<ext> blob.bin: gzip compressed data, was "data.out", from Unix, last modified: Fri Jan 24 21:10:12
I dont have any more details about gzip file atm (timestamp of creation, comments, version...)
More details about html and hex string:
Here is beginning nad ending of hex string on onion (2014.01.29 01:25 http://avowyfgl5lkzfj3n.onion)
1f8b0808a4c8e2520003646174612e6f757400ecfd65545c5db72e8a169a e0c12d40d020c1dd09c1ddb580e0eeee24b8bb6b702778e1047702145eb8 17ee0e87f75bfbb67bdadef7b6b3cf9ff3add5ce7a5a9b3565688d31677f ... . ... f684b4849898c8417188c84121b0a0c0819d7c7c3b7709eddcc1c3cbcbcd cdcdc3c9c5cdc5c5036c9d84d559d68bd56340cf40eff21ee007f31bf3bf 001633b8008ff02d00
For more details look in logs below this post: [01:14] <nopd> do you know that onion 4 is back up?
Here are few (again contadictory) posts of people who saw string on onion 4 and 5 on Jan 29th. If you solve any contradictions (actual html tags, that additionl string someone mentioned, why gzip apeared corupt for some...) please note that in wikia below.
[08:53] <akame> onion 5 had this html
[08:53] <akame> <html><head>
[08:53] <akame> <meta http-equiv="content-type" content="text/html; charset=ISO-8859-1"></head><body>-----BEGIN PGP SIGNED MESSAGE-----
[08:53] <akame> Hash: SHA1
[01:29] <hoagie> no additional html just the text
[01:20] <nopd> http://tinypic.com/r/16ih9n8/8
[01:20] <ext> in addition to the large blob there is this in the end: 001633b8008ff02d00
[01:31] <ext> I mean the clearnet proxy might add the additional html
[01:31] <ext> anyway, the hex string is the same
<ext> blob.bin: gzip compressed data, was "data.out", from Unix, last modified: Fri Jan 24 21:10:12 2014
<ext> sibilance: it appears to be gzip but fails to decompress
[01:27] <snibbib> here, got it up on infotomb: https://infotomb.com/ujvmg
[01:27] <hoagie> https://infotomb.com/uhsc3
[01:33] <modusponies> https://infotomb.com/gxvhz includes my screenshot
[01:33] <oh5fsz> it uncompressed fine for me
Problem 1 solved, there were NO html tags!
[16:29] <hoagie> last nights onions DIDN'T have any html.. just raw data.. if u saw html it was added by your browser/firebug/whatevertooluuse[16:15]
<KineticX> should see the raw html download as the .html file i posted
[16:16] <KineticX> from last night
[16:17] <KineticX> q4utgdi2n4m4uim5.onion.html
[16:17] <KineticX> should have the raw download
[16:32] <akame> NiceLurk indeed i got it by saving output in firefox - so maybe auto-generated?
[16:33] <NiceLurk> akame: yeah must be something like this, when you save as html it adds html tags, you have to right click and wiev page source to get original page content
001633b8008ff02d00 string are just last bytes of gzip file, since number of bytes is not multiple of 30, or 60 characters, (string was divided in 60 char long lines)
Analysis of new Onion 4 data
Onion 4 contained 4 different JPGs: https://infotomb.com/qjiqh [https://infotomb.com/3vw2u https://infotomb.com/3vw2u https://infotomb.com/609xy https://infotomb.com/8do0b
Things found on the onions: http://sigmaninestudios.com/3301
Another pastebin with links to onion 4 backups http://pastebin.com/uLT3drh2
Rune Decoding

Substitution key for onion 4 koan
Runes were not in plain english. Decoding them only using Gematria Primus didnt yield readable result.
It was found that it was encrypted with substitution cipher. It was first solved by <mourn> and <sibilance>
Here is the key for substitution: http://pastebin.com/fdjd14pK
Substitution is similar than it was on onion 2 but key was shifted by 3 runes down. To see this just compare this key and from onion 2 key from onion 2
Onion 4 Transcription of runes by sibilance...essen... Page 1: A Koan: A man decided to go and study with a maste r. He went to the door of the master. "Who are yo u who wishes to study her e" asked the master. The stude nt told the master his name. "That is not what you are, tha t is only what you are cal led. Who are you who wish es to study here" he aske Page 2: d again. The man thought for a moment and replied "I am a professor". "That is what you do, not what you are." replied the master. "Who ar e you who wishes to stud y here". Confused the man th ought some more. Finally, he answered, "I am a human b eing". "That is only your spe cies, not who you are. wh Page 3: o are you who wishes to study here", asked the maste r again. after a moment of th ought the professor repl ied "I am a consciousness i nhabiting an arbitrary body ". "That is merely what you a re not who you are. Who a re you who wishes to stu dy here". The man was getting ir ritated. "I am," he started, Page 4: but he could not think of anything else to say, so he tra iled off. After a long pause the master replied, "Then yo u are welcome to come stu dy" An Instruction: Do four unreasonable things each da y:
A Koan A man decided to go and study with a master. He went to the door of the master "who are you who wishes to study here?" asked the master. The student told the master his name. "That is not what you are that is only what you are called. Who are you who wishes to study here?" he asked again. The man thought for a moment, and replied "I am a professor." "That is what you do, not what you are" replied the master. "Who are you who wishes to study here?" Confused, the man thought some more. Finally, he answered, "I am a human being." "That is only your species, not who you are. Who are you who wishes to study here?" asked the master again. After a moment of thought, the professor replied "I am a consciousness inhabiting an arbitrary body." "That is merely what you are not who you are" who are you who wishes to study here?" The man was getting irritated. "I am," he started, but he could not think of anything else to say, so he trailed off. After a long pause the master replied "then you are welcome to come study." An Instruction Do four unreasonable things each day.
New pages for Liber Primus book from onion 4
Exif and outguess
Exif of all 4 pages from onion 4.
http://regex.info/exif.cgi?dummy=on&imgurl=https%3A%2F%2Finfotomb.com%2Fqjiqh.jpg

4 jps from onion 4, levels up filter, 3rd one is showing outguess artefacts
http://regex.info/exif.cgi?dummy=on&imgurl=https%3A%2F%2Finfotomb.com%2F3vw2u.jpg
http://regex.info/exif.cgi?dummy=on&imgurl=https%3A%2F%2Finfotomb.com%2F609xy.jpg
http://regex.info/exif.cgi?dummy=on&imgurl=https%3A%2F%2Finfotomb.com%2F8do0b.jpg
First, Second and Fourth show Resolution 400 pixels/inch
Third one that contained outguess shows Resolution 1 pixels/None, like all previous jpgs with outguess did
Picture is showing jpg artefacts on all 4 pages from onion 4. Jpgs are made 4 times smaller, but you can still clearly see how artefacts outguss makes are much more notable about corners, and you can notice that jpg compression of jpg with outguess is much worse than of other three jpgs. (outguess by defoult saves at 75% jpg compression, if -p <param> is not used)
Filesizes also show similar pattern:
- onion5jpg1 805kB
- onion5jpg2 805kB
- onion5jpg3 624kB
- onion5jpg4 708kB
Outguess and a Transposition Cipher
While outguess did return data for all images, only the 3rd of them seemed to be readable. The message was:
For those who have fallen behind: TL BE IE OV UT HT RE ID TS EO ST PO SO YR SL BT II IY T4 DG UQ IM NU 44 2I 15 33 9M Good luck. 3301
It was quickly figured out that this was a message encoded with a transposition cypher. When arranged in a rectangle with 7 columns for each letter, then decoding using the key 1736254 (where each number is the character position), we see the message as:
TOBELIEVETRUTHISTODESTROYPOSSIBILITYQ4UTGDI2N4M4UIM59133
Or, written in a more readable form :
To believe truth is to destroy possibility - http://q4utgdi2n4m4uim5 - 9133
Tool that was used: http://tholman.com/other/transposition/
Unanswered questions
- Why was 9133 at the end of the URL to onion 5?
- 9133 is prime number (as is 3319)
- We assumed it was a port number, but it didn't work
A new Onion (Onion 5)

Interconnectedness - Cicada 3301
The new onion contained a *LARGE* amount of hex data -- enough to crash Firefox as it were. The data can be found here. Not only that, but the message was signed and confirmed to be the same legitimate Cicada key (which verified that we can "trust" it).
Hex string on onion 5
Once again, analysis revealed this to be a .mp3 file, in the same style of last year's mp3 file, but this year's is called Interconnectedness.
- Violin resembling instrument in last third of the song is reversed guitar. SImilar as 761.mp3 in 2013 had. Although this song is much less palindromic-like than one in 2013 was.
Mp3 ID3 tags:
artist: 3301 song: Interconnectedness title: Interconnectedness
The word "Interconnectedness" has a Gematria value of 772, and the song is 277.133 seconds long.
Things found on the onions: http://sigmaninestudios.com/3301
ID3 tag doesnt store any dates, and since file was in hex string, date of creation in NTFS is made only after you create file in hex editor. So no way to determine when mp3 was recorded and compressed. (i am not sure about that, if i am wong plese fix that sentence)
[20:13] <nazgul> The complete story of onion5: All of my notes and the links to the downloaded data: http://pastebin.com/pFLQhtXQ
PGP signature
String on onion 5 has been PGP signed with legit cicada 3301 key.
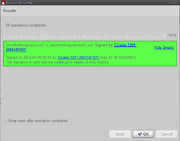
PGP signature of mp3 string on onion5
Timestamp of signature is: 18.1.2014 02:03(local time zone of OS in time of signing)
Before that day nobody was able to see exact same string on onion5.
Analysis of the song
Analysis of the song is currently ongoing.
[16:26] <nopd> https://infotomb.com/614ww <-- midi from the notes in the mp3 file
[20:49] <nopd> @nikkler_ https://infotomb.com/b6bk3 a mididump
[23:07] <nopd> detailed midi format http://pastebin.com/zifC5neQ
mp3 stego: all ancient windows software...
- http://spoox.org/wp/2007/02/12/a-few-ways-of-watermarking-mp3-files/
- http://embeddedsw.net/zip/OpenPuff.zip
- http://tenet.dl.sourceforge.net/project/mp3stegz/mp3stegz/mp3stegz-1.0stable/mp3stegz-1.0.zip
- http://www.petitcolas.net/fabien/software/MP3Stego_1_1_18.zip
zoanthall tried mp3stegz and mp3stego, no dice
the first frame is fake lame header, from byte 37-627 is possible ciphertext (unlikely) or code.
these 590 bytes have very skewed bit distribution (lot more 0s even if full 0 bytes are not counted), maybe flags?
- SheCalledMePaul: its in D minor, and DADGAD tuning btw if that helps you [03:27am]
- austintrigue: that last refrain from the guitar is being played backwards[03:12am] SheCalledMePaul: there was backwards guitarplaying in 761.mp3 as well[03:12am]
- counterhash: Playing the two mp3s on top of each other in Audacity produces nothing of interesct [06:17am]
- modusponies: for those focusing on the audio, you can do a lot more beyond a spectrogram http://cnmat.berkeley.edu/link/9943
- length of song is 277.133 seconds. 277133 is prime
- snibbib: also, song is 277 seconds long. the title "Interconnectedness" adds up to 772 in the gematria [06:12am]
- zoanthall: i've tried mp3stegz and mp3stego, no dice
- high freq cutoff checked - PersonalKilljoy: http://i.imgur.com/eXNLU1h.jpg
- the size of the mp3 is 665187 bytes = 2 * 3325937
- split channel dumps analysed
- padding bytes analysed (this is still open if it contains ciphertext)
counterhash: Anyone know why we have all of the 55s at the end for padding? Is it a normal LAME function or?[06:45am] Mothwing: No, that's not normal in LAME, look at the other mp3s we've received as hex text, they were all encoded with LAME too.
More detailed analysis of Interconnectedness mp3 and onion 4
Titanpads from time of solving onion 4 string and onion 5 string:
http://titanpad.com/bQwpt7NDUP
http://titanpad.com/2IDiePVoFH <--conatains also of factual data on onion 4 and 5
http://titanpad.com/5szzye0A9V <--this one is about onion 5 and onino 6
[20:13] <nazgul> The complete story of onion5: All of my notes and the links to the downloaded data: http://pastebin.com/pFLQhtXQ
earlier hints on onion 5 akame: so you remember the matrix jpeg page 4? it had no passless outguess [12:04am] akame: when you run outguess [12:04am] akame: it says data length 58152 [12:04am] akame: familiar? [12:05am] akame: now outguess says iextracted data length too long [12:05am] akame: so i modified the outguess source code [12:05am] akame: to dump the data buffer [12:05am] akame: the first 4 bytes match the new onion jpg outguessses!!! akame: p4 matrix jpg forced outguess with bytelength 58152: https://infotomb.com/pnid9 [12:18am] concise summary: https://infotomb.com/xgh2q fwiw any outguess key on new onioin 4 images and old p4 produces same seed and length [03:20am] akame: so does it mean they have the same key? onion 5 http://thepeoplesrepublicofeurope.bandcamp.com/ [06:51am]austintrigue: what generated the bandcamp link? a decrypt? a person? [12:54am] KineticX: http://thepeoplesrepublicofeurope.bandcamp.com/track/night-of-the-cicada onion 4 came online at 0:05gmt 29/01/2014 html data via firefox https://infotomb.com/1fn08 html stripped data is hexdump of gzip archive also see http://pastebin.com/A0dWX1Qi (nazgul) cat avowyfgl5lkzfj3n.onion.html |perl -pe 's/^.*body\>//;s/\<\/bo.*//' |grep -v head > o4.hex xxd -r -p o4.hex > o4.gz gunzip o4.gz extract 4 images from the uncompressed data python jpaeger.py < o4 mv unknown.stdin.000.jpg o4.1.jpg mv unknown.stdin.001.jpg o4.2.jpg python doc/rev.py o4 > o4.rev python jpaeger.py < o4.rev mv unknown.stdin.000.jpg o4.3.jpg mv unknown.stdin.001.jpg o4.4.jpg outguess -r o4.3.jpg o4.3.og outguess -r o4.4.jpg o4.4.og /* you can run jpaeger.py with filename as argument, it will append number and jpg to each output file. this save having to rename file --teefs */ there was no OOB data in between the 4 images in o4.3.jpg: outguess is ASCII: see below the other 3 are exactly 58152 bytes long nazgul: I have already XORed the 58152 bytes outguesses of the onion4 images 00,01 and 03, nothing useful 3 non-ascii outguesses outguesses in zip archive here https://infotomb.com/svu5q (idontworkfor3301) the 3 non-ascii outguesses: o4.[124].jpg.og https://infotomb.com/k11ys https://infotomb.com/pqdcz https://infotomb.com/6mtc6 Eve57: I checked 98 combinations of the three outguesses and the three 256 byte strings. [05:39am] ext: there is a large portion of the beginning that is similar [05:40am] nazgul: My filenames are following the extraction routine as detailed in http://pastebin.com/A0dWX1Qi nazgul: I am looking for any file headers in the onion4 outguesses (exept the ASCII that gave us onion5). No useable (as in images/text/compressed data/mp3) file headers found in onion4.image00.outguess (58152 bytes) nazgul: No useable (as in images/text/compressed data/mp3) file headers found in onion4.image01.outguess (58152 bytes) nazgul: No useable (as in images/text/compressed data/mp3) file headers found in onion4.image03.outguess (58152 bytes) nazgul: No useable file headers (for images/text/compressed data/mp3) found in onion4.image00.jpg (823807 bytes) XORed with any of the 256 byte strings or their byte-order reversed copies at all possible offsets. Minimum entropy is 6.89 Note: outguessXX == onion4.imageXX.outguess.dat file: outguess00_XOR_outguess01.dat: data file: outguess00_XOR_outguess03.dat: data file: outguess01_XOR_outguess03.dat: data file: outguess00_XOR_outguess01_XOR_outguess03.dat: data Nothing of interest found, only binary data. XORed all three 58152 byte non ascii outguesses from onion4 with the onion5.mp3 at all possible offsets. I scanned for file headers but found no readable files. The minimum entropy is around 7.9 in all cases. An extensive analysis of the three non-ASCII outguesses in combination with the three 256 byte strings from onions 2,3 and 4 can be found at http://pastebin.com/vkaf3KWY iII|out: https://infotomb.com/3kcte.txt [07:30am] onecool: these outguesses XORed are producing weird results.. [07:30am] iII|out: that's a diff of 1+3 and 2+3 [07:31am] https://infotomb.com/3kcte.txt akame: 0096 2e0a 418d 3733 1236 4774 b16a 118f 6f96 f384 e148 0a00 [07:35am] onecool: [00:40] <onecool> if onion address is 16 characters + '.' + 5(onion) [06:53am] onecool: [00:40] <onecool> 22 characters total [06:57am] strings are identical from 0 upto byte 1571 (prime), then for 22 bytes 1 and 2 are identical then for another 22 bytes all 3 identical, tand from then on all seems random tried all ways possible to get these 22 bytes to decipher to an onion (16 + . + onion) seemed such a sweet idea - but found nothing 4 pages of runic script SheCalledMePaul: 4 new runes here: http://pastebin.com/Swwv9V6Q (ext: https://github.com/ext/jpegsplit <-- I use this tool to extract concaternated jpegs [12:56am]) rune translations of 4 runic pages by sibilance http://titanpad.com/WZsXR2TIjI Eve57: <Eve57>I just tried this: http://jocr.sourceforge.net/ [02:52am] Eve57: <Eve57>That is an OCR software that can learn new alphabets on the fly. [02:52am] Eve57: <Eve57>Whenever there is a unknown symbol it will ask as what it should be recognized. [02:52am] Eve57: <Eve57>Or you can even manually build a database - just a directory with images and a text file that contains the mapping file - symbol. [02:56am] Eve57: And I removed the border around the text manually. [02:57am] Eve57: gocr -p ./db/ -m 130 -m 256 001.pnm sibilance: cleaned up runes translation: https://gist.github.com/anonymous/ab917b4c225859c8c2b2 [03:17am] The latest rune images all used the same template as the same discrepancies appear in the same place on all of them outguess leading to onion 5 in o4.3.jpg: outguess is ASCII: nazgul: In image02.jpg I find the following outguess (Note that there is no GPG signature): http://pastebin.com/kqfUPAvV [12:52am] For those who have fallen behind: TL BE IE OV UT HT RE ID TS EO ST PO SO YR SL BT II IY T4 DG UQ IM NU 44 2I 15 33 9M Good luck. 3301 akame: i got the message decyphered [01:44am] SheCalledMePaul: the whole thing D: [01:44am] SheCalledMePaul: lol [01:44am] ss23: akame: And? [01:46am] shadowfix_: Waiting for it... [01:46am] SheCalledMePaul: lol [01:46am] akame: transposition cypher [01:47am] SheCalledMePaul: what is key length [01:48am] akame: 7 col 8 rows 1736254 [01:48am] akame: to believe truth is to destroy possibility [01:48am] truth: wat [01:48am] sir_phobos: what are the numbers [01:50am] dead: nice work [01:50am] akame: the onion is: r2dliu: http://q4utgdi2n4m4uim5.onion/ [01:58am] transposition cypher 0 6 2 5 1 4 3 T O B E L I E V E T R U T H I S T O D E S T R O Y P O S S I B I L I T Y Q 4 U T G D I 2 N 4 M 4 U I M 5 9 1 3 3 leading to onion 5 http://q4utgdi2n4m4uim5.onion/ (currently offline) onion 5 html data via firefox https://infotomb.com/3y1c8 html stripped data dump: https://infotomb.com/ooxyo (including GPG siganture, which is valid) or https://infotomb.com/sjpce. when decrypted: https://infotomb.com/his5u file called interconnectedness [02:11am] poincare__: http://dump.sidvind.com/onion5.mp3 - ha! code in guitar? interconnectedness, an mp3 file A mirror of the song is here on Youtube - http://www.youtube.com/watch?v=ActGqDxBD4A SheCalledMePaul: its in D minor, and DADGAD tuning btw if that helps you [03:27am] austintrigue: that last refrain from the guitar is being played backwards[03:12am] SheCalledMePaul: there was backwards guitarplaying in 761.mp3 as well[03:12am] counterhash: Playing the two mp3s on top of each other in Audacity produces nothing of interesct [06:17am] modusponies: for those focusing on the audio, you can do a lot more beyond a spectrogram http://cnmat.berkeley.edu/link/9943 length of song is 277.133 seconds. 277133 is prime snibbib: also, song is 277 seconds long. the title "Interconnectedness" adds up to 772 in the gematria [06:12am] zoanthall: i've tried mp3stegz and mp3stego, no dice high freq cutoff checked - PersonalKilljoy: http://i.imgur.com/eXNLU1h.jpg the size of the mp3 is 665187 bytes = 2 * 3325937 counterhash: Anyone know why we have all of the 55s at the end for padding? Is it a normal LAME function or?[06:45am] Mothwing: No, that's not normal in LAME, look at the other mp3s we've received as hex text, they were all encoded with LAME too. all source files: http://sigmaninestudios.com/3301/ Eve57: (Negative) result of XORing the three strings against the four images from tonight. Now running against the MP3. http://pastebin.com/08WXw5gj [04:40am] <Eve57>Final result of XOR started last night; images and MP3: http://pastebin.com/7j73TupH OutGuess noise: http://pastebin.com/fe1GqNMT unused cues on the way: 9133 was redundant end after onion 5 in deciphered outguess text instruction on page 4 of onion 4 images: 9133 is prime, so is 3319 277133 is also prime (length of mp3) amone: do four things unreasonable each day has a gematria value of 1429 which is a prime [03:08am] amone: 14293319 is also a prime The Rune Text: (from the four new images) https://gist.github.com/anonymous/ab917b4c225859c8c2b2 Onion 4 Transcription of runes by sibilance...essen... Page 1: A Koan: A man decided to go and study with a maste r. He went to the door of the master. "Who are yo u who wishes to study her e" asked the master. The stude nt told the master his name. "That is not who you are, tha t is only what you are cal led. Who are you who wish es to study here" he aske Page 2: d again. The man thought for a moment and replied "I am a professor". "That is what you do, not what you are." replied the master. "Who ar e you who wishes to stud y here". Confused the man th ought some more. Finally, he answered, "I am a human b eing". "That is only your spe cies, not who you are. wh Page 3: o are you who wishes to study here", asked the maste r again. after a moment of th ought the professor repl ied "I am a consciousness i nhabiting an arbitrary body ". "That is merely what you a re not who you are. Who a re you who wishes to stu dy here". The man was getting ir ritated. "I am," he started, Page 4: but he could not think of anything else to say, so he tra iled off. After a long pause the master replied, "Then yo u are welcome to come stu dy" An Instruction: Do four unreasonable things each da y:
↓ ↓ ↓ ↓↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓↓ ↓ ↓ ↓↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓ ↓
OK BOYS AND GIRLS Looks like in night from 30. Jan to 31 Jan alot of things happen, I also misssed it all, so be patient with wikia.
Also it looks we are in individual part of Cicada 3301 puzzle now
WE WILL BE ON PAGE 7 FROM NOW ON
↑ ↑ ↑The happening (FACTUAL PART OF WIKIA 2014 PAGE 6) above this line ↑ ↑ ↑
↓ ↓ ↓ ↓ The happening (BRAINSTORMING and OPEN LEADS) bellow this line ↓ ↓ ↓ ↓
Maybe cipher in mp3 is similar than one in 2012 midid puzzle was
After the RSA puzzle, people who submitted the correct answer to their individual RSA puzzle (each person had different "n") to the onion page received another email with a MIDI puzzle. The MIDI puzzle and solution can be found there: http://pastebin.com/4nrDxVXk.
If you don't understand how the cipher was solved ask in #33012013 or #cicadasolvers. BAsicly it was substitution cipher where one tone in midi was one letter. Midi consist two songs. Second one is encrypted text from Chorus of Blakes Poem A Song of Liberty (Let the Chorus be your guide to the depths : was hint). First midi song was encrypted text players had to decrpy, with unique set of words on the end:
verygood you have proven to be most dedicated to come this far to attain enlightenment create a gpg key for your email address and upload it to the mit key servers then encrypt the the following word list using the cicada three three ero one public key sign it with your key send the ascii armoured ciphertet to the gmail address from which you received your numbers your words are [unique list of words here] garden ball house cat shore back head galon
Lurkers midi puzzle from 2012 example:
[18:40] <NiceLurk> https://infotomb.com/oq17i here is midi from 2012 [18:40] <NiceLurk> http://pastebin.com/4nrDxVXk here is how it was solved
<PersonalKilljoy> spectorgram
[13:33] <PersonalKilljoy> guys does the structure of mp3 forces patterns in data? [13:34] <PersonalKilljoy> since after loading mp3 as 'data' into gimp and with some width/height playing around you can get white lines <PersonalKilljoy> http://i.imgur.com/eXNLU1h.jpg <PersonalKilljoy> i'm not sure if spek doesn't lie there since audacity doesn't recognize anything above 20 khz, and spek claims something is higher than that [10:55] <PersonalKilljoy> http://i.imgur.com/8q9Xxaw.jpg [10:56] <PersonalKilljoy> in the middle at about 2:20 [10:56] <PersonalKilljoy> see?
on 2:20 to 2:30 isnt something:
PS: Change the frequency range in the settings
Eve57 XORING
[13:36] <Eve57> Final result of XOR started last night; images and MP3: http://pastebin.com/7j73TupH OutGuess noise: http://pastebin.com/fe1GqNMT
[13:37] <Eve57> Nothing, btw. ^^
<Anoniem4l>
[14:18] <Anoniem4l> Yes I did all possible combinations.
[14:18] <Anoniem4l> I found some good tool to XOR instantly file to file.
[14:18] <Anoniem4l> 36 XOR outputs in total.
[14:18] <Anoniem4l> 15 of them final.
[14:18] <NiceLurk> and you got legit ID3 tag file beginnings?
[14:18] <Anoniem4l> Yes.
[14:19] <Anoniem4l> At all finals.
[14:19] <NiceLurk> also link the tool and put it on tolls page so otehr can try it also
[16:44] <Anoniem4l> I gave it, sec.
[16:44] <Anoniem4l> http://www.nirsoft.net/utils/xorfiles.html
[16:44] <TaiiwoBot> ^ XorFiles v1.0 ^
[16:45] <Anoniem4l> Works like a charm with wine.
Mp3 stego tools
[05:39] <erfwerf> guys there's a stego tool for mp3: http://www.petitcolas.net/fabien/steganography/mp3stego/
[16:49] <Pilgrim> There's another stego tool for MP3s
[16:49] <Pilgrim> OpenPuff
[16:50] <Pilgrim> http://embeddedsw.net/OpenPuff_Steganography_Home.html
Some XORING with no results
[20:05] <nazgul> No useable file headers (for images/text/compressed data/mp3) found in onion4.image00.jpg (823807 bytes) XORed with any of the 256 byte strings or their byte-order reverse copies at all possible offsets
A detailed description of all the XORing can be found in http://pastebin.com/vkaf3KWY
In short, the three 256 byte strings from onions 2,3 and 4 and their byte-order reversed versions have been XORed against the three non-ASCII 58152 byte outguesses from onion4 at each possible offset (i.e. offset = 0 byte, 1 byte, ...). No readable files were found and the lowest entropy is around 6.9.
The 256 byte strings and the reversed order versions have also been XORed against the 4 JPG images found on onion4 at every possible offset. Again, no readable files were discovered and the minimal entropy was around 6.9.
Further, the three 58152 byte non-ASCII outguesses from the onion4 JPGs were XORed against each other in every combination. No readable files were found.
The mp3 file from onion 5 has been XORed at all possible offsets with the three 58152 byte non-ASCII outguesses from onion4. A search for file headers of jpg/png/gzip/zip/bzip2 and for text files was conducted. No readable files could be found. The minimum entropy was about 7.9.
Some more XORING with interesting result but not sure if anything
(((JPG#1XOROnion5MP3)XORJPG#2)XORJPG#4)XOROnion5MP3. http://speedy.sh/yYXj5/4xorsTotal
New pages of the primus // re-write this, please
We got a new onion (http://ut3qtzbrvs7dtvzp.onion/), from it we got a long string which was transformed into 4 new .jpeg pages which had runic messages which read as follows:
======page 1
the loss of diuinity: the circumference. prpractices. three behaviors. which. avse. the. loss.of divinity
<consumption>: we.consume.too.much. because.we.belive. the. following. two.errors. within.the.deception:
1 we. do. not. have. enough: or. there. is not. enough
======page 2
2 we.have.what.we.have.now.by.luck: and.we.will.not.be.strong.anough.later.to.obtain.what.we.need.
most. things.are.not.worth.consuming>
<preservation> we.preserve. things. because.we.believe. we. are.weak: if. we. lose. them. we. will.not.be.strong. enough.to.gain.them.again: this.is.the.deception.
=========page 3
most.things.are.not.worth.preserving:
<adherence> we.follow. dogma. so. that. we. can. belong. and.be.right: or.we. follow. reason. so .we. can. belong. and.be.right:
there is nothing to be right about: to belong is death>
it is the behaviors consumtion preservation: and adherence
=====page 4 : ..CE THAT HAVE US LOSE OUR PRIMALITY AND THUS OUR DIVINITY. SOME WISDOM: AMASS GREAT WEALTH NEVER BECOME ATTACHED TO WHAT YOU OWN. BE PREPARED TO DESTROY ALL THAT YOU OWN. AN INSTRUCTION: PROGRAM YOUR MIND. PROGRAM REALITY
// please edit this, but do not change the actual data.
Jokes That Were On This Page
Have been moved here: CICADA_3301_2014_PUZZLE_FACTS_THE_END_JOKES




